Quantum
Resolve problems that cannot be efficiently calculated with existing supercomputers to quickly solve problems in areas where answers were difficult to find
Post Quantum Cryptography(PQC)
Next-Generation Encryption Technology Responding to Quantum Threats
Replacing existing public key encryption algorithms with cryptographic technologies that can be safely used even in a quantum computing environment,
All existing security systems need to transition to PQC (Post-Quantum Cryptography) before the development of quantum computers is completed.

Quantum computing optimization algorithms such as Shor algorithm and Grover algorithm shorten the factorization time and pose a threat to modern public key-based encryption systems.

Problems occur when [migration time + security time] is greater than the Collapse Time
- x security time
- Time to keep your data safe
- y migration time
- How long does it take to transition to a safe solution?
- z decay time
- How long will it take for a quantum computer to break currently used cryptography?
Establishment of a quantum-resistant security system
-
PKI Authentication solution
-
-
Post-Quantum Era Quantum-Resistant Security System
-
Quantum-resistant digital signature algorithm
-
- Quantum resistance
- Quantum-resistant key setting algorithm Pilot application cases for domestic companies: LGU+, KISA nProtect, East Security MIST
-
- Perfect replacement for the public key-based security system already in use
- Establishment of a safe security authentication infrastructure without performance degradation
-
- Signature authentication speed
- Signature generation 63 times faster than the current international standard public key encryption RSA
- Signature verification 6 times faster than ECDSA digital signature algorithm
Quantum-resistant PKI authentication solution for IoT security
-
1
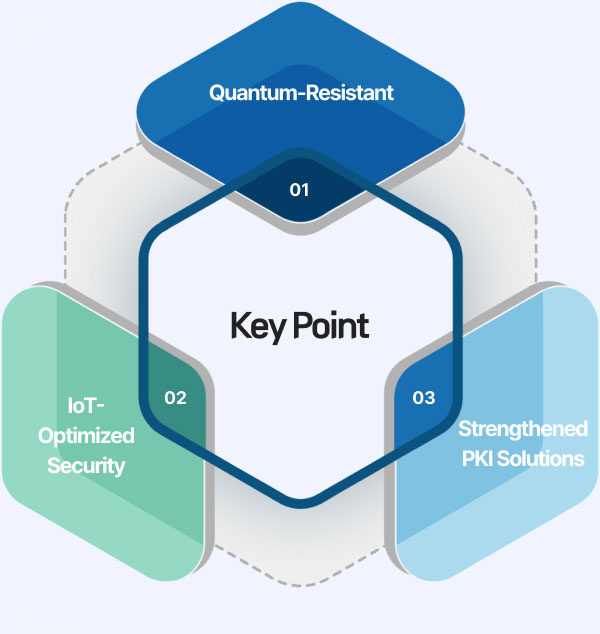
Securing a leading position in the quantum security market with leading-edge technology acquired through technology transfer.
-
2
Security solutions optimized for the entire range of IoT environments.
-
3
Enhancing PKI public key-based solutions with quantum-resistant algorithms.

